My friend invited me to lunch and mentioned the word "cafe", but I didn't go.
After 4 hours, I noticed a post related to cafes in my Facebook news feed:
This post isn't very popular and I haven't heard the word "Cafe" for a long time, I can't even recall the last time. So I realized this post is not a coincidence, not again (something I type in ChatGPT also shows similar ads, either OpenAI or my keyboard is selling my data, as expected~).
So I quickly dumped adb logcat, hoping the relevant logs hadn't disappeared yet. Fortunately, it did retain the
05-16 19:39:17.603 log from the previous night: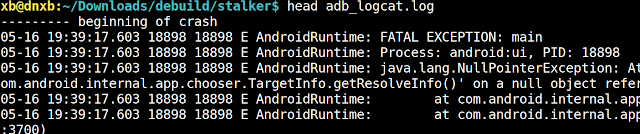
The next thing I found is quite intriguing:
I recall my friend speaking to me around 12:30 pm (not sure of the exact time, but it was before 1 p.m.), and coincidentally, a suspicious log appears here that is too blatant to ignore!
The
com.vivo.smartshot is a system app on my Vivo phone. I extracted the APK using that package name and found its app label is 'S-Capture' (gi is grep -i):And yes, it has the microphone/record audio permission:
When I go to the system app settings, its permissions can't be turned off since it's a "system app"!
What is the "S-capture" app really? The Vivo site shows:
I'm only able to take a screenshot by swiping down with three fingers, but I don't see the floating dialogue for recording. It might be a different version, but I don't see any log showing SmartShot.
CVE of Vivo smartshot:
And the Calling a method in the system process without a qualified user is just a warning, not an indication of operation failure, as shown in AOSP:
I initially suspected that S-Capture was the problematic app, or that
another app was exploiting the CVE associated with it.







